A number of malicious Android apps that have been installed over 50,000 times from the official Google Play Store are used to target banks and other financial entities.
The Lease Banking Trojan, nicknamed Octois said to be a re-image of another Android malware called ExobotCompact, which, in turn, is a “lightweight” replacement for its predecessor Exobot, Dutch mobile security firm ThreatFabric said in a report shared with The Hacker News.
Exobot is also said to have paved the way for a separate descendant called Coper, which was initially discovered targeting Colombian users around July 2021, with new infections targeting Android users in different European countries.
“Coper malware applications are modular in design and include a multi-step infection method and numerous defensive tactics to survive removal attempts,” cybersecurity firm Cyble noted in an analysis of the malware last month.

Like other Android banking Trojans, rogue apps are nothing more than droppers, whose main function is to deploy the malicious payload embedded in them. The list of Octo and Coper droppers used by several threat actors is below –
- Pocket Screencaster (com.moh.screen)
- Fast Cleaner 2021 (vizeeva.fast.cleaner)
- Play Store (com.restthe71)
- Postbank Security (com.carbuildz)
- Pocket Screencaster (com.cutthousandjs)
- BAWAG PSK Security (com.frontwonder2), and
- Installing the Play Store app (com.theseeye5)
These apps, which pose as a Play Store app installer, screen recording, and financial apps, are “powered by inventive delivery systems”, distributing them through the Google Play Store and via fraudulent landing pages that allegedly alert users to download a browser update.
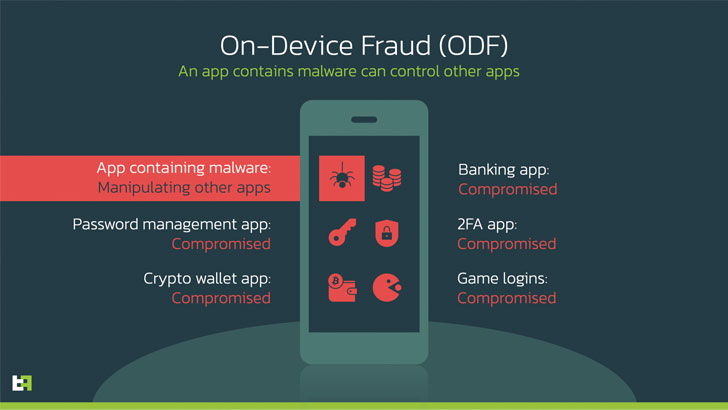
The droppers, once installed, act as a conduit to launch Trojans, but not before asking users to enable Accessibility Services that allow it a wide range of capabilities to exfiltrate sensitive information from compromised phones.
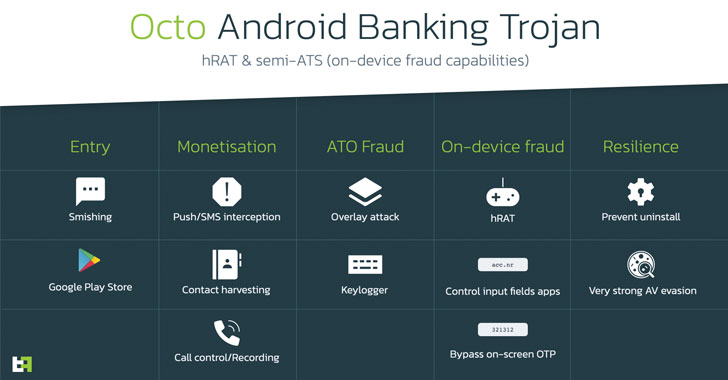
Octo, the revised version of ExobotCompact, is also equipped to perform device fraud by taking remote control of devices by leveraging accessibility permissions as well as Android’s MediaProjection API to capture content screen in real time.
The ultimate goal, ThreatFabric said, is to trigger “the automatic initiation of fraudulent transactions and its authorization without manual efforts on the part of the operator, thereby enabling fraud on a much larger scale.”
Other notable features of Octo include logging keystrokes, performing overlay attacks on banking apps to capture credentials, collecting contact information, and persistence measures to prevent uninstallation and evade antivirus engines.

“The rebranding to Octo erases previous ties to the leaked Exobot source code, inviting multiple threat actors looking for an opportunity to lease a supposedly new and original Trojan,” ThreatFabric noted.
“Its capabilities endanger not only explicitly targeted apps that are targeted by an overlay attack, but any app installed on the infected device, as ExobotCompact/Octo is able to read the content of any app displayed on the device. screen and provide the actor with enough information to remotely interact with it and perform on-device fraud (ODF).”
The findings follow the discovery of a separate Android bankbot named GodFather – sharing overlaps with banking trojans Cereberus and Medusa – which has been observed targeting banking users in Europe under the guise of the Default Settings app for transfer funds and steal SMS messages, among others.
On top of that, a new analysis published by AppCensus found 11 apps with over 46 million installs that were implemented with a third-party SDK named Coelib that captured clipboard content, GPS data, email addresses, phone numbers and even the MAC address of the user’s modem router and network SSID.