Threat actors have been distributing malicious apps under the guise of seemingly harmless shopping apps to target customers of eight Malaysian banks since at least November 2021.
The attacks involved creating fraudulent but legitimate-looking websites to trick users into downloading the apps, Slovakian cybersecurity firm ESET said in a report shared with The Hacker News.
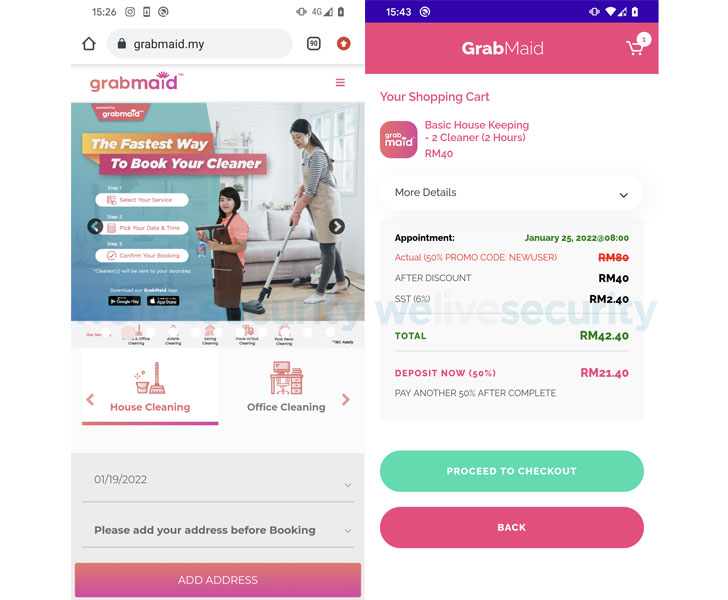
The copycat websites impersonated cleaning services such as Maid4u, Grabmaid, Maria’s Cleaning, Maid4u, YourMaid, Maideasy and MaidACall and a pet store named PetsMore, all of which are aimed at users in Malaysia.

“Threat actors use these fake online store apps to phish banking credentials,” ESET said. “The apps also forward all SMS messages received by the victim to malware operators in case they contain 2FA codes sent by the bank.”
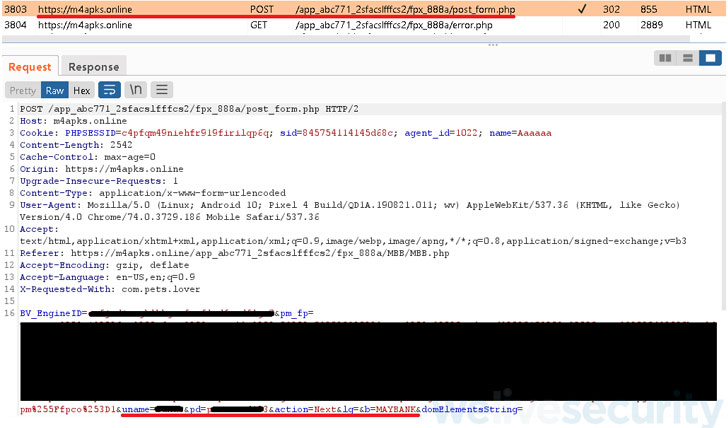
The targeted banks are Maybank, Affin Bank, Public Bank Berhad, CIMB bank, BSN, RHB, Bank Islam Malaysia and Hong Leong Bank.
The websites, served via Facebook ads, invite visitors to download what the attackers claim are Android apps available on the Google Play Store, but in reality redirect them to malicious servers under their control.
It should be noted here that the attack relies on the precondition that potential victims enable the non-default “Install unknown apps” option on their devices for it to succeed. What’s more, five of the abused services don’t even have an app on Google Play.
Once launched, the apps prompt users to log into their accounts, allowing them to place fake orders, after which options are presented to complete the payment process including a transfer of funds from their bank accounts.

“After choosing the direct transfer option, the victims are presented [with] a fake FPX payment page and asked to choose their bank from the eight Malaysian banks provided and then enter their credentials,” said Lukáš Štefanko, Malware Researcher at ESET.
The ultimate goal of the campaign is to steal banking credentials entered by users and exfiltrate them to the server controlled by the attacker, while displaying an error message stating that the username or password entered is not valid.
Additionally, the fake apps are designed to access and forward all SMS messages received by the users to the remote server in case the bank accounts are secured with two-factor authentication.
“Although the campaign is exclusively targeting Malaysia at the moment, it may expand to other countries and banks later,” Štefanko said. “At the moment attackers are looking for bank credentials, but they could also enable the theft of credit card information in the future.”